Nethemba public security research projects (2007-2015)
There will be no brute-force attack capability in this application. The first block of the first sector of an original MIFARE Classic tag is read-only i.e. But there are special MIFARE Classic tags that support writing to the manufacturer block with a simple write command. This App is able to write to such tags and can therefore create fully. Mifare Classic Offline Cracker Vijay Superum Pournamiyum 1080p Torrent Download Celestion Pa Speakers Murder By Death Shirt English Grammar Active And Passive Voice.



MfocGUI - MiFare Offline Cracking GUI. The first tool is called mfocGUI, which has many repos on GitHub, but no source came with this particular compiled EXE, so again use at your own risk! As the title indicates, this tool will have a decent chance of cracking Mifare “Classic” S50 1k and S70 4k chip keys. Mfcuk - MiFare Classic Universal toolKit (MFCUK). Mfoc - Mifare Classic Offline Cracker. Termux-fedora - A script to install a Fedora chroot into Termux. AutoSploit - Automated Mass Exploiter. AutoPixieWps - Automated pixieWps python script. Exploitdb - The official Exploit Database repository. May 11, 2019 Mifare Classic Offline Cracker. Contribute to vk496/mfoc development by creating an account on GitHub.
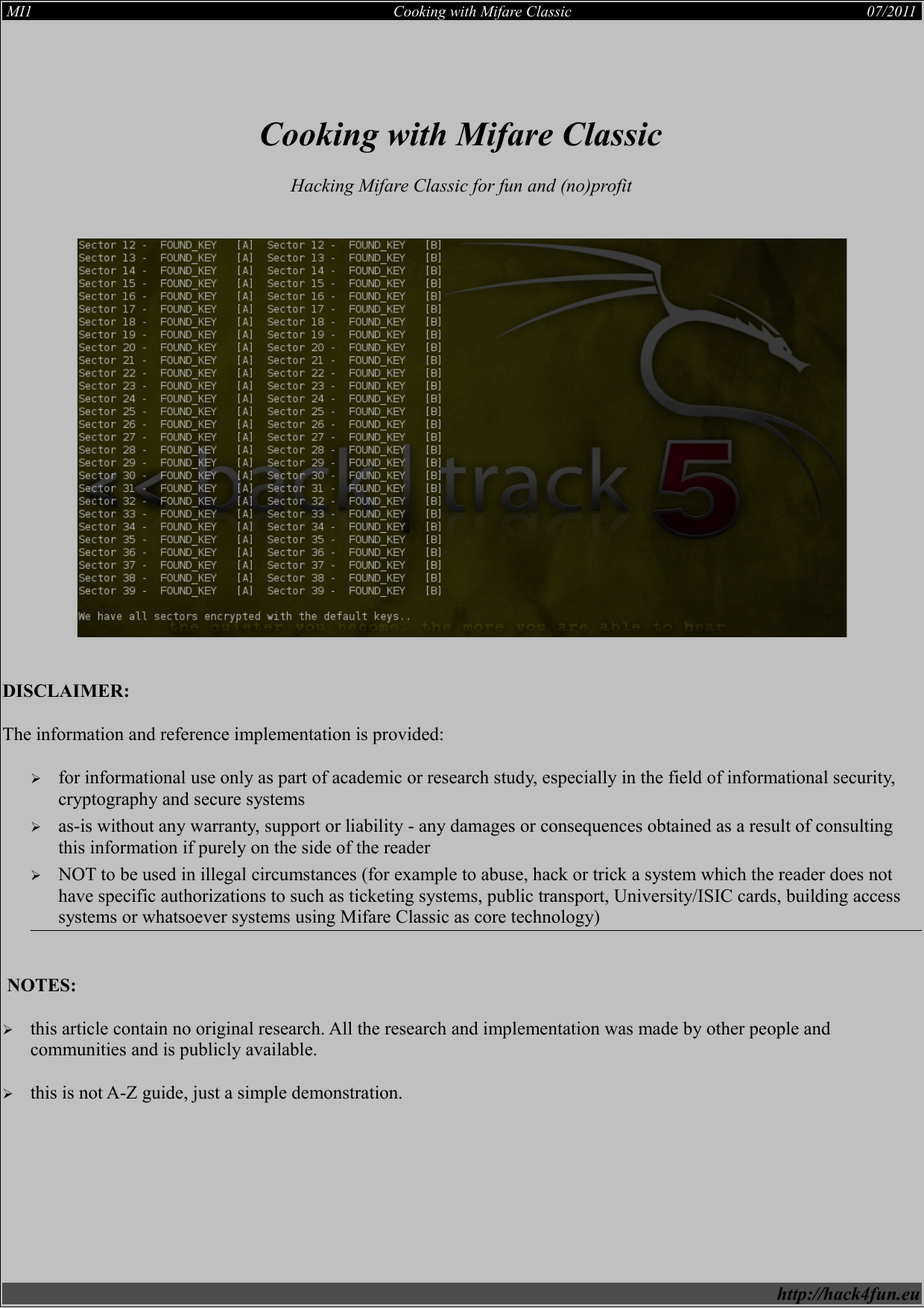
Since 2007 when Nethemba was started, we have begun to focus on public research projects. One of the reasons was that we were aware of a lack of security in technologies most people use daily, the second one, was a need of being different compared to our IT security competition, especially in Czech and Slovak republic. During the period 2007-2015, we published many security-related articles, blogs, and papers. We would like to discuss the most important ones with the considerable impact.
Mifare Classic Offline Cracker Barrel
Nethemba public security research projects (2007-2015)
Mifare Classic Offline Cracker Bar
Since 2007 when Nethemba was started, we have begun to focus on public research projects. One of the reasons was that we were aware of a lack of security in technologies most people use daily, the second one, was a need of being different compared to our IT security competition, especially in Czech and Slovak republic. During the period 2007-2015, we published many security-related articles, blogs, and papers. We would like to discuss the most important ones with the considerable impact.