Maltego is a data mining tool that mines a variety of open-source data resources and uses that data to create graphs for analyzing connections. The graphs allow you to easily make connections between information such as name, email organizational structure, domains, documents, etc. Maltego uses Java so it can run on Windows, Mac, and Linux. Full Maltego Classic/XL add-on. Integration into customers enviroment. Explore Products. Start your investigation now. Have more questions? Maltego is an example which uses OSINT to gather information.Maltego, is an open source intelligence and forensics application and shows how information is connected to each other. Another advantage of this tool is that the relationship between various types of information can give a better picture on how they are interlinked and can also help. Maltego is a visual link analysis tool that, out the box, comes with open source intelligence (OSINT) plugins, called transforms. The tool offers real-time data mining and information gathering as well as the representation of this information on a node based graph making patterns and multiple order connections between said information easily identifiable. With the Read More »Maltego.
With paper trails having turned digital, person of interest investigations have become a complex game of cat-and-mouse. Navigating such digital landscape can become challenging for law enforcement agencies and investigators alike. Simultaneously, it is becoming easier and easier for criminals and malicious actors to hide behind fake online identities.
With Maltego, investigators can quickly and easily link seemingly disparate leads and build a comprehensive map of a target person’s digital footprint. Integrated with a variety of OSINT, social intelligence, and identity data sources, Maltego is the perfect tool to quickly obtain and analyze the digital presence of a person of interest.
In this tutorial, we demonstrate how to conduct person-of-interest investigations starting with just a name or alias, using a standard personal reconnaissance process in Maltego.
Personal Recon Process for Person of Interest (POI) Investigation 🔗︎
For this tutorial, we are going to conduct a person of interest investigation based on the name (or alias) “Prabal Panjabi.” He is a friend who would like to map out and clean up his digital footprint and has asked for our help. We will attempt to find all online data around Prabal using Maltego.
First, we will map the full online presence for the target’s name or alias by looking at relevant websites and images.
Second, we will attempt to discover any personal information such as email addresses or phone numbers from the target’s online footprint.
Finally, once we can confirm the target’s identify, we will pivot into advanced person-of-interest databases to obtain more specific identity intelligence.
Getting Started: Transforms Hub Items Required for This POI Investigation 🔗︎
We will use the following Hub items in this tutorial: Maltego Standard Transforms, Social Links CE, and Pipl. If you would like to follow along in your own Maltego Client, please ensure that these Hub items are installed.
To access Maltego Standard Transforms and Social Links CE, simply install them in the Transform Hub on your Maltego Desktop Client. You can access Pipl data in Maltego by purchasing our data bundles or a Pipl data connector.
Watch the Tutorial in Action 🔗︎
Watch the video demonstration of this tutorial on our YouTube channel! Read along in this article for the complete documented process.
Let’s get started!
Step 1: Mapping the Online Footprint of the Person of Interest 🔗︎
We begin this investigation with a Phrase Entity as the starting point and change the input value from default to the target alias, “Prabal Panjabi.” To increase the accuracy of our Transform results, we use some search engine Dorking techniques and add quotation marks around the input text.
We then run the To Websites [Using Search Engine] Transform on this Phrase Entity.
This Transform queries the Bing search engine, which returns all websites mentioning our quoted search term, “Prabal Panjabi”.
Running this Transform has returned 256 websites, including social media profiles or public pages like Facebook, Instagram, Wikipedia, Twitter, and even IMDB.
Next, we run the To URLs [Using Search Engine] Transform on these Website Entities to find the related URLs.
From the returned URL Entities, it seems that our friend Prabal is an actor in the Bollywood film industry. To verify this, we need more information.
We can obtain information from these URLs in two ways:
- First, we run the To Entities [IBM Watson] Transform, which will extract Entities like organizations, locations, email addresses, people, and images that are found on the webpages.
- Second, we run the To Images [Found on web page] Transform, which finds and returns all images on the webpages.
From these Transforms results, we have already made a few interesting discoveries. For example, the Facebook profile pins our target’s location in Mumbai and associates a few artists with this person. The Wikipedia page pins the target in Chandigarh, another city in India, and associates Disney with this person.
The Transforms has also returned a number of images that might help us identify the target.
The most interesting result we have uncovered thus far is that the Prabal Panjabi Person Entity is shared by all our website sources.
Next, let’s see if we can pivot from this Person Entity to finding more personal details.
Step 2: Finding Personal Information from Known Online Presence of the Target 🔗︎
First, we run the To EmailAddress [Bing] Transform on the Person Entity. We could specify an email domain in the pop-up window if we already know which email services this person is using, but in our case, we leave it blank to find as many results as possible.
The Transforms have returned a number of email addresses, including one that matches our target’s alias. This could legitimately be the email address of our target.
We can verify the email address by running the Verify and fraud-check email address [IPQS] Transform. The result will be populated in the Detail View to the right.
The IPQS Transform results tell us that the email address does exist and has not been involved in fraud activities. It is now safe to assume that this is indeed a personal email address.
Pivoting from An Email Address to Social Accounts Investigation 🔗︎
So far, we have been running this investigation using Maltego Standard Transforms, which are shipped for free with our software. However, Maltego also has a wide variety of third-party data integrations that that can enrich various investigations.
From this email address, we can pivot into social accounts investigation to find the social footprints of our target using the Social Links CE data integration.
We run the [Skype] Search by email Transform to find Skype accounts associated with this email. We then run the [Skype] User Details Transform to extract available information of this account.
We have now discovered the Skype account of Prabal Panjabi, who is a 30-year-old male living in Mumbai, India. We also have a picture of him, which will make identifying relevant leads much easier.
Step 3: Diving into Advanced Identity Intelligence to Understand the Target’s Real-life Profile 🔗︎
We can now take our findings and pivot from here using Pipl, the largest identity database in the world. Querying the Pipl database may help us find the real-life identity of our target and understand the person’s current profile as well as their historical background.
Pipl Identity Database and How to Query it Using Maltego 🔗︎
Pipl Transforms in Maltego take an input such as a name, email address, phone number, and others and search within their database to find matching person profiles. These are returned to a Maltego graph as Person Entities. From a Pipl Person Entity, we can further query the database to discover other personal information such as career history, associated persons, hobbies, and more.
A POI Investigation using Pipl Transforms 🔗︎
We start with the Prabal Panjabi Person Entity and run the Search Person [Pipl] Transform.
The Transform has returned a few Pipl Possible Person Entities with orange dot overlays. These are persons stored in the Pipl database that might be a match to our target.
We know that our target is 30 years old and we have a Skype profile picture of him. This helps us narrow our focus to three of the Possible Person Entities returned.
We select all three and run the Resolve search pointer [Pipl] Transform, which resolves the Possible Person Entities into Pipl Person Entities (with green dot overlays) that are an exact match.
To see whether these actually represent our target person, we run the Expand in Full and Expand in Detail Transform Sets. These Transforms will return all information for these Person Entities stored in the Pipl database.
The two Transforms have returned a host of information ranging from physical addresses, email addresses, phone numbers, social media accounts, and some Pipl Tag Entities. Since most of the results are shared between the three Pipl Person Entities, we can be sure that all three Person Entities are of the same identity.
Let’s take a closer look at who Prabal Panjabi is.
The email address returned by the Pipl Transforms matches the email address we discovered previously, hereby confirming that our investigation results are accurate.
According to the addresses, Prabal Panjabi seems to have lived in both India and Virginia, USA. There are a few phone numbers that we could pivot further from. We also have a few Twitter accounts related to our target.
What could also prove very interesting are the Pipl Tag Entities. These Entities represent the hobbies, interests, and other notable information about Prabal Panjabi.
For example, going down the list, we can see that Prabal Panjabi seems to have shown interest in a few movies and series such as How I Met Your Mother, Kungfu Panda, Batman, The Hangover, and Prison Break. He also seem to like watermelons.
While these particular interests are harmless, little nuggets of information like these from a person’s past (or present) can help us to glean a complete picture of, and get closer to a person and his or her interests.
If we want to know the source of such information, we can select these Tag Entities and run the To Source Origin [Pipl] Transform. Based on the results, we know that Pipl collected this information from Prabal Panjabi’s Facebook activities.
And that wraps up our person-of-interest investigation demo.
Next Steps: Enrich the POI Investigation with More OSINT Data 🔗︎
This is an example of a personal recon process investigators can perform using Maltego.
Recap of the POI Investigation Process 🔗︎
To quickly recap, we started with a name and found websites that mention the name. From these webpages, we retrieved possible location information and the personal identity of our target.
Next, we discovered an email address which in turn led to a Skype account which provided us with a picture of our target person and disclosed more personal details such as age.
Finally, we pivoted into Pipl’s identity database to obtain more detailed information for the person-of-interest.
Pivoting to Other OSINT Data 🔗︎
From the different Entities returned to our graph, we could of course investigate deeper and wider, such as pivoting into reverse image search or conducting a network footprint using the email address. This would help us to map an extensive online and infrastructure network of the person of interest.
If we are conducting the person of interest investigation for fraud, we could also look at the target’s business relationships using the OpenCorporates and WhoisXML data integrations. We showed such a use case in our joint webinar with Pipl.
The purpose of your investigation will help you to decide what next steps to take.
We hope you enjoyed this demonstration of a person of interest investigation. Don’t forget to follow us on Twitter and LinkedIn and sign up to our email newsletter to stay updated on latest tutorials, use cases, and webinars!
Happy investigating!
Of course, hacking has evolved too: nowadays you can find a lot of automated OSINT Tools that can help anyone with security research and intel reconnaissance in a way that just wasn’t possible twenty years ago.
In past decades, ethical hacking and penetration testing were performed by only a few security experts. Now almost anyone can report security incidents. Ethical hacking tools allow you to scan, search and find the flaws and vulnerabilities within any company to help make their systems and applications more secure (as seen in the recent Top CVE’s exploited in the wild post published a few weeks ago).
Today we’ll explore the best ethical hacking tools used by modern security researchers.
Do you want to access the ultimate OSINT tool?Maltego Ce
Learn how SurfaceBrowser™ can help you to explore Domains, DNS Servers, IP addresses and much more.15 Ethical Hacking Tools You Can’t Miss
We’ve compiled some of the most popular penetration testing tools to help you through the first steps of a security investigation. You’ll find some of the classic tools that seem to have been around forever and some new tools that might not be familiar.
1. John the Ripper
John the Ripper is one of the most popular password crackers of all time. It’s also one of the best security tools available to test password strength in your operating system, or for auditing one remotely.
This password cracker is able to auto-detect the type of encryption used in almost any password, and will change its password test algorithm accordingly, making it one of the most intelligent password cracking tools ever.
This ethical hacking tool uses brute force technology to decipher passwords and algorithms such as:
- DES, MD5, Blowfish
- Kerberos AFS
- Hash LM (Lan Manager), the system used in Windows NT / 2000 / XP / 2003
- MD4, LDAP, MySQL (using third-party modules)
Another bonus is that JTR is open source, multi-platform and fully available for Mac, Linux, Windows and Android.
2. Metasploit
Metasploit is an open source cyber-security project that allows infosec professionals to use different penetration testing tools to discover remote software vulnerabilities. It also functions as an exploit module development platform.
One of the most famous results of this project is the Metasploit Framework, written in Ruby, which enables you to develop, test and execute exploits easily. The framework includes a set of security tools that can be used to:
- Evade detection systems
- Run security vulnerability scans
- Execute remote attacks
- Enumerate networks and hosts
Metasploit offers three different versions of their software:
- Pro: ideal for penetration testing and IT security teams.
- Community: used by small companies and infosec students.
- Framework: the best for app developers and security researchers.
Supported platforms include:
- Mac OS X
- Linux
- Windows
3. Nmap
Nmap (Network Mapper) is a free open source security tool used by infosec professionals to manage and audit network and OS security for both local and remote hosts.
Despite being one of the oldest security tools in existence (launched in 1997), it continues to be actively updated and receives new improvements every year.
It’s also regarded as one of the most effective network mappers around, known for being fast and for consistently delivering thorough results with any security investigation.
What can you do with Nmap?
- Audit device security
- Detect open ports on remote hosts
- Network mapping and enumeration
- Find vulnerabilities inside any network
- Launch massive DNS queries against domains and subdomains
Supported platforms include:
- Mac OS X
- Linux, OpenBSD and Solaris
- Microsoft Windows
4. Wireshark
Wiresharkis a free open-source software that allows you to analyze network traffic in real time. Thanks to its sniffing technology, Wireshark is widely known for its ability to detect security problems in any network, as well as for its effectiveness in solving general networking problems.
While sniffing the network, you’re able to intercept and read results in human-readable format, which makes it easier to identify potential problems (such as low latency), threats and vulnerabilities.
Main features:
- Saves analysis for offline inspection
- Packet browser
- Powerful GUI
- Rich VoIP analysis
- Inspects and decompresses gzip files
- Reads other capture files formats including: Sniffer Pro, tcpdump (libpcap), Microsoft network monitor, Cisco Secure IDS iplog, etc.
- Supported ports and network devices: Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI.
- Protocol decryption includes but not limited to IPsec, ISAKMP, Kerberos, SNMPv3, SSL/TLS, WEP, and WPA/WPA2
- Exports results to XML, PostScript, CSV, or plain text

Wireshark supports up to 2000 different network protocols, and is available on all major operating systems including:
- Linux
- Windows
- Mac OS X
- FreeBSD, NetBSD, OpenBSD
5. OpenVAS
OpenVAS (also known as the old classic “Nessus”) is an open-source network scanner used to detect remote vulnerabilities in any hosts. One of the best-known network vulnerability scanners, it’s very popular among system administrators and DevOps and infosec professionals.
Main features
- Powerful web-based interface
- +50,000 network vulnerability tests
- Simultaneous multiple host scanning
- Able to stop, pause and resume scan tasks
- False positive management
- Scheduled scans
- Graphics and statistics generation
- Exports results to plain text, XML, HTML or LateX
- Powerful CLI available
- Fully integrated with Nagios monitoring software
While its web-based interface allows it to be run from any operating system, a CLI is also available and works well for Linux, Unix and Windows operating systems.
The free version can be downloaded from the OpenVAS website, but there is also a commercial enterprise license available from the Greenbone Security (parent company) website.
6. IronWASP
If you’re going to perform ethical hacking, IronWASP is another great tool. It’s free, open source and multi-platform, perfect for those who need to audit their web servers and public applications.
One of the most appealing things about IronWASP is that you don’t need to be an expert to manage its main features. It’s all GUI-based, and full scans can be performed in only a few clicks. So, if you’re just getting started with ethical hacking tools, this is a great way to start.
Some of its main features include:
- Powerful GUI-based interface
- Web scan sequence recording
- Exports results into HTML and RTF file format
- 25+ different web vulnerabilities
- False positive and negative management
- Full Python and Ruby support for its scripting engine
- Can be extended by using modules written in C#, Ruby, and Python
- Supported platforms: Windows, Linux with Wine, and MacOS using CrossOver
7. Nikto
Nikto is another favorite, well-known as part of the Kali Linux Distribution. Other popular Linux distributions such as Fedora already come with Nikto available in their software repositories as well.
This security tool is used to scan web servers and perform different types of tests against the specified remote host. Its clean and simple command line interface makes it really easy to launch any vulnerability testing against your target, as you can see in the following screenshot:
Nikto’s main features include:
- Detects default installation files on any OS
- Detects outdated software applications.
- Runs XSS vulnerability tests
- Launches dictionary-based brute force attacks
- Exports results into plain text, CSV or HTML files
- Intrusion detection system evasion with LibWhisker
- Integration with Metasploit Framework
8. SQLMap
sqlmap is a cool cyber-security tool written in Python that helps security researchers to launch SQL code injection tests against remote hosts. With SQLMap you can detect and test different types of SQL-based vulnerabilities to harden your apps and servers, or to report vulnerabilities to different companies.
Its SQL injection techniques include:
- UNION query-based
- time-based blind
- boolean-based blind
- error-based
- stacked queries
- out-of-band
Main features:
- Multiple database server support: Oracle, PostgreSQL, MySQL and MSSQL, MS Access, DB2 or Informix.
- Automatic code injection capabilities
- Password hash recognition
- Dictionary-based password cracking
- User enumeration
- Get password hashes
- View user privileges and databases
- Database user privilege escalation
- Dump table information
- Executes remote SQL SELECTS
Check out the next video to see the true power of SQLMap using the sqlmap out-of-band injection working with Metasploit integration against Microsoft SQL Server:
9. SQLNinja
SQLNinja is another SQL vulnerability scanner bundled with Kali Linux distribution. This tool is dedicated to target and exploit web apps that use MS SQL Server as the backend database server. Written in Perl, SQLNinja is available in multiple Unix distros where the Perl interpreter is installed, including:
- Linux
- Mac OS X & iOS
- FreeBSD
SQLninja can be run in different types of modes such as:
- Test mode
- Verbose mode
- Fingerprint remote database mode
- Brute force attack with a word list
- Direct shell & reverse shell
- Scanner for outbound ports
- Reverse ICMP Shell
- DNS tunnelled shell
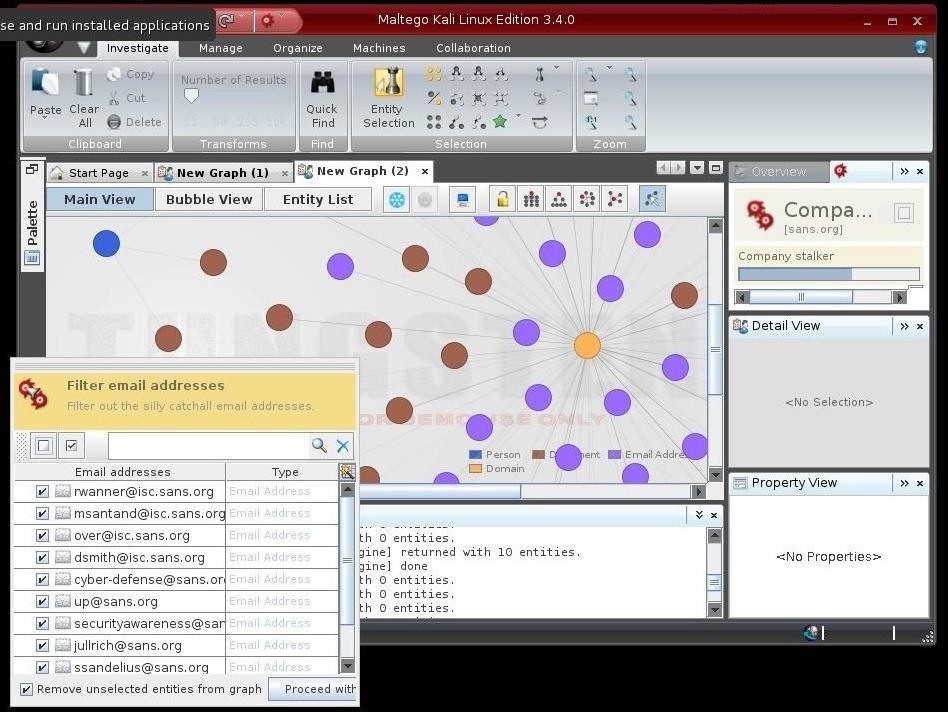
10. Maltego
Maltego is the perfect tool for intel gathering and data reconnaissance while you’re performing the first analysis of your target.
In this case, it can be used to correlate and determine relationships between people, names, phone numbers, email addresses, companies, organizations and social network profiles.
Along with online resources like Whois data, DNS records, social networks, search engines, geolocation services and online API services it can also be used to investigate the correlation between internet-based infrastructures including:
- Domain names
- DNS servers
- Netblocks
- IP addresses
- Files
- Web Pages
Main features include:
- GUI-based interface
- Analyzes up to 10.000 entities per graph
- Extended correlation capabilities
- Data sharing in real time
- Correlated data graphics generator
- Exports graphs to GraphML
- Generates entity lists
- Can copy and paste information
This application is available for Windows, Linux, and Mac OS, and the only software requirement is to have Java 1.8 or greater installed.
11. Burp Suite
Burp Suite may well be one of the most popular platforms used in the security testing and bug bounty hunting industry today. It includes several hacking tools that enable bug bounty hunters and security researchers to detect, map, analyze, and ultimately exploit vulnerabilities within the attack surface of any application.
Its main features include:
- Automated penetration testing
- Manual penetration testing techniques
- Interception of browser-based data
- Fast fuzzing and brute forcing attacks
- Automated vulnerability scanning
- Ability to perform attack analysis
- Productivity tools
12. NetStumbler
NetStumbler (also known as MiniStumbler) is one of the top ethical hacking tools used to analyze IEEE 902.11g, 802, and 802.11b networks on Windows operating systems.
Often called “the Swiss Army knife of wireless network analysis”, this hacking tool is now one of the most popular pieces of software used to find, pivot and cross-relate data from a wireless network, enabling researchers and IT administrators to find, analyze, configure and harden their wireless networks.
Key NetStumbler features and capabilities include:
- Find and explore access points
- Access point filters
- Identify access point network configuration
- Detect illegal/unauthorized access points over the network
- Find root cause of network interferences
- Analysis of signal strength over the network
13. AirCrack-ng
AirCrack-ng is a respected Wifi security suite for home and corporate security investigations. It includes full support for 802.11 WEP and WPA-PSK networks and works by capturing network packets. It then analyzes and uses them to crack Wifi access.
For old-school security professionals, AirCrack-ng includes a fancy terminal-based interface along with a few more interesting features.
Main features:
- Extensive documentation (wiki, manpages)
- Active community (forums and IRC channels)
- Support for Linux, Mac and Windows Wifi detection
- Launches PTW, WEP and Fragmentation attacks
- Supports WPA Migration Mode
- Fast cracking speed
- Multiple Wifi card support
- Integration with 3rd party tools
As a bonus, it comes bundled with a lot of Wifi auditing tools including:
- airbase-ng
- aircrack-ng
- airdecap-ng
- airdecloak-ng
- airdriver-ng
- aireplay-ng
- airmon-ng
- airodump-ng
- airolib-ng
- airserv-ng
- airtun-ng
- easside-ng
- packetforge-ng
- tkiptun-ng
- wesside-ng
- airdecloak-ng
14. Ettercap
Ettercap is a network interceptor and packet sniffer for LAN networks. It supports active and passive scans as well as various protocols, including encrypted ones such as SSH and HTTPS.
Other capabilities include network and host analysis (like OS fingerprint), as well as network manipulation over established connections -- which makes this tool great for testing man-in-the-middle attacks.
Main features
- Active and passive protocol analysis
- Filters based on IP source and destination, Mac and ARP addresses
- Data injection into established connections
- SSH and HTTPS encryption-based protocols
- Sniffs remote traffic over GRE tunnel
- Extensible with plugins
- Protocol supports include Telnet, FTP, Imap, Smb, MySQL, LDAP, NFS, SNMP, HTTP, etc.
- Determines OS name and version
- Able to kill established LAN connections
- DNS Hijacking
15. Canvas
Canvas is a great alternative to Metasploit, offering more than 800 exploits for testing remote networks.
Main features
- Remote network exploitation
- Targets different kind of systems
- Targets selected geographic regions
- Takes screenshots of remote systems
- Downloads passwords
- Modifies files inside the system
- Escalates privileges to gain administrator access
Maltego Ce
This tool also lets you use its platform to write new exploits or use its famous shellcode generator. It also integrates an alternative to nmap called scanrand, which is especially useful for port scanning and host discovery over mid to large networks.
Supported platforms include:
- Linux
- MacOSX (requires PyGTK)
- Windows (requires Python and PyGTK)
Maltego
Summary
Maltego For Windows
Software companies reap the most benefits from the rise of automated ethical hacking tools and penetration testing utilities, giving them more ways to increase system security every day.
Maltego Community Edition
Automated tools are changing the way hacking is evolving, making ethical penetration testing easier, faster and more reliable than ever. Penetration testing and reporting activities now play a crucial role in the process of identifying security flaws in remote or local software — enabling company owners to quickly prevent vulnerabilities from running wild all over the Internet.